Stop an ATTACK before it happens..
Use Breach and Attack Simulation to test & discover security gaps
Choose a Simulation:


Attacks
Test if attack behaviors are detected, or customize the packages to further test alternate behaviors.

Data loss
Run simulated data loss scenarios to test data loss prevention solutions or to test incident response processes.

Control Validation
Validate if controls are effectively detecting known attack vectors.

Ransomware
Run emulated ransomware scenarios to test incident response processes, or more immersive table-top exercises.

Threat simulation
Run simulations of emerging threats to see how protection systems are protecting the environment.

Counter-forensics
Test incident response processes to determine what threat actors can see during the triage and forensics process.
Run the simulation package
-
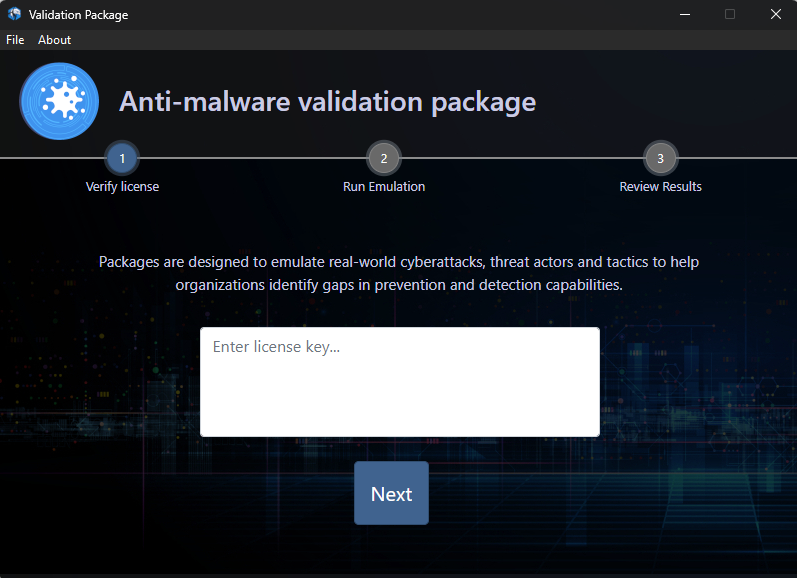
Enter license key
Enter the temporary package license key (each valid for 7 days).
-
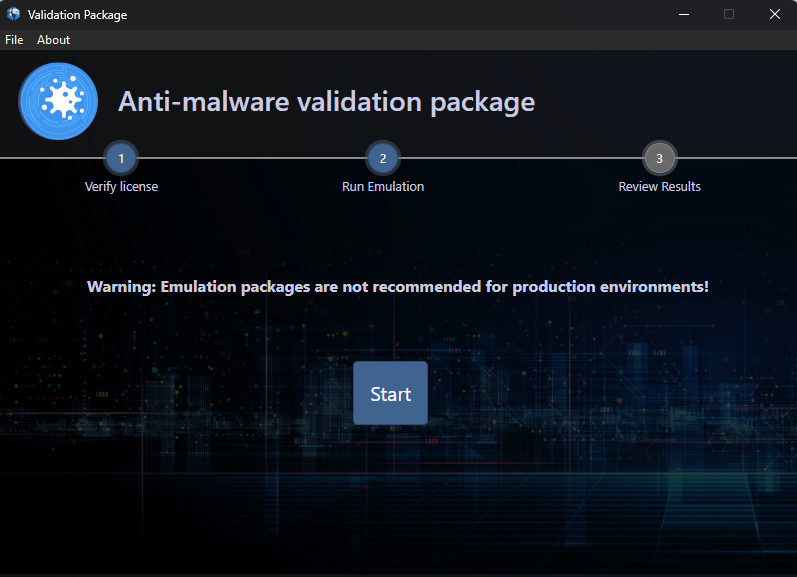
Run the package
Click run, or if available, also select customization options.
-
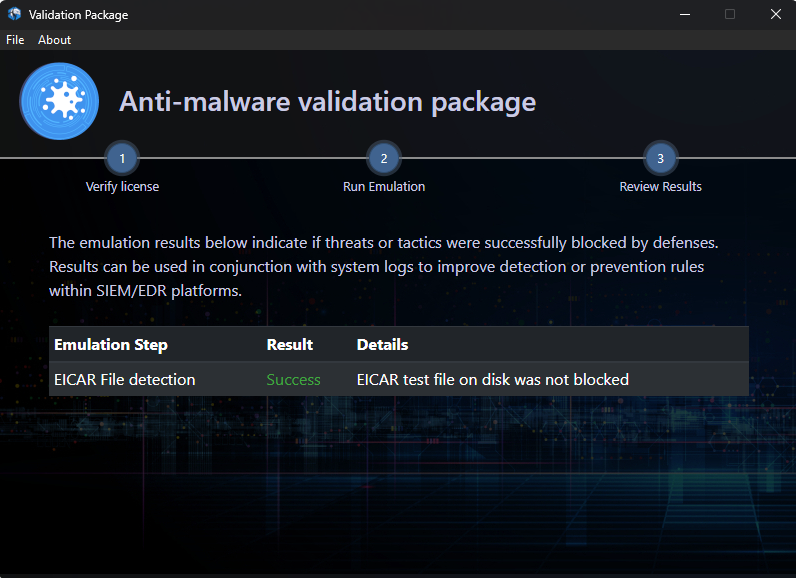
Review the results
Review which functions successfully ran, then use the results to review controls in your endpoint protection systems to evaluate effectiveness and completeness of detection.
Recently added packages:
Anti-malware validation
This package runs tests that validate if anti-malware software can effectively prevent known malware on an endpoint.